 The Gartner report predicts that in 2013, the total investment of big companies in the world will increase to 34 billion U.S. dollars, a year-on-year increase of 8 times. In the first half of this year, market research agency IDC predicted that the market for big data technology and services will climb from 3.2 billion U.S. dollars in 2010 to 16.9 billion U.S. dollars in 2015. According to IDC, this will achieve an annual growth rate of 40% and will be 7 times the growth rate of the entire IT and communications industries. The trend of big data can be said to be self-evident. We believe that it is more important to extract business value from these big data.
The Gartner report predicts that in 2013, the total investment of big companies in the world will increase to 34 billion U.S. dollars, a year-on-year increase of 8 times. In the first half of this year, market research agency IDC predicted that the market for big data technology and services will climb from 3.2 billion U.S. dollars in 2010 to 16.9 billion U.S. dollars in 2015. According to IDC, this will achieve an annual growth rate of 40% and will be 7 times the growth rate of the entire IT and communications industries. The trend of big data can be said to be self-evident. We believe that it is more important to extract business value from these big data. Big data, also called huge data, refers to the huge amount of data involved that cannot be accessed through the current mainstream software tools. It can be retrieved, managed, processed, and organized in a reasonable time to help the company make business decisions. Active purpose information. The "big" here has several layers of meaning. It can describe the size of the organization. What's more important is that it defines the scale of the IT infrastructure in the enterprise. The industry places endless expectations on the application of big data. The more business information is accumulated, the more The greater the value. Therefore, the strategic significance of big data technology is not to master huge data information, but to specialize in these meaningful data. In other words, if the big key data compared to an industry, then this industry to achieve profitability, to improve the data "processing capacity" through "process" to achieve "value-added" data.
For the security industry, network-connected equipment systems in safe cities, intelligent traffic management, environmental protection, hazardous goods transportation monitoring, food safety monitoring, or government agencies, large enterprise workplaces, etc. will most likely be the largest Data resources. With the advancement of safe cities, smart cities and other projects, surveillance cameras have spread all over the streets, and security monitoring has become increasingly demanding for high-definition, intelligence, networking, and digitization, and the amount of data has naturally grown rapidly.
For the big data generated by the video surveillance industry, Chen Wenming, chairman and president of Shenzhen Zhongxin Technology Co., Ltd., stated that Zhongyuxin developed the first domestic 1080P HD network camera at the end of November 2012, and the speed can be achieved. 60 frames per second, such a camera video files generated in a month up to 1.8T, if the number of cameras or system integration caused more data types, the burden of long-term storage is generally difficult for enterprises to bear. The dramatic increase in storage pressure, on the one hand, places high demands on the storage capacity of storage servers. In addition to the ability to store large amounts of data, it also faces more data types. Sources of these data include online transactions, social networking activities, and automation. Sensors, mobile devices, scientific instruments, and more. On the other hand, it is particularly important for data management. The data is always growing. When there is a demand to find a certain segment of monitoring, it must be combined with intelligent retrieval and intelligent analysis technologies in order to extract more effectively and the cost will be correspondingly higher. Improve a lot.
In addition to the large scale of data, "big data" also means having a huge number of files. So how do you manage the file system metadata layer accumulation is a problem, if not handled properly will affect the scalability and performance of the system, and there is a traditional NAS system bottleneck. Fortunately, the object-based storage architecture does not have this problem. It can manage billions of files in one system, and it will not suffer from metadata management like traditional storage. Object-based storage systems also have With wide-area scalability, you can deploy and form a cross-region large-scale storage infrastructure in multiple locations.
Although big data is one of the hot applications on the Internet, in the security industry, due to its own business characteristics and the limited R&D direction of manufacturers in the industry, “big data†technology has not been deeply applied in the security industry. The application and development direction of big data in security projects is an excellent opportunity for most security companies.
In the face of ultra-large-scale monitoring applications, as a data storage system, while ensuring data security, reliability, and stability, application performance should be guaranteed, such as multi-channel video concurrent writing, file retrieval, video playback, and data management. Wait. The analysis and mining of big data is one of the common support points between smart cities and smart security. An integrated urban management platform based on deep data mining is needed to break the barriers of traditional industry information islands.
In the information age, data is an important production factor, just like other elements such as capital, labor, and raw materials. As a general demand, it is no longer limited to the application of certain special industries. Companies in various industries are collecting and using a large amount of data analysis results to reduce costs as much as possible, improve product quality, increase production efficiency, and create new products. By analyzing the data collected directly from the product testing site, not only can the company help improve the design, but it can also surpass his competitors by analyzing the customer's behavior in depth and then comparing a large amount of market data.
At present, many companies recognize the potential value of big data analytics applications, include more data sets into the system for comparison, allow more people to share and use these data, and comprehensively analyze multiple data objects from different platforms. The storage infrastructure including the global file system can help users solve data access problems. The global file system allows multiple users on multiple hosts to concurrently access file data, which may be stored in multiple locations. Different types of storage devices in order to create more business value.
The pace of the information age is very fast. The China Internet Network Information Center (CNNIC) released the "28th Statistical Report on Internet Development in China". As of June 2012, the proportion of mobile Internet users in the overall Internet population reached 65.5%, becoming As an important component of Chinese Internet users, the speed of the mobile Internet is very alarming. The quiet coming of the big data era will inevitably set off a commercial situation in various industries. Security is no exception.
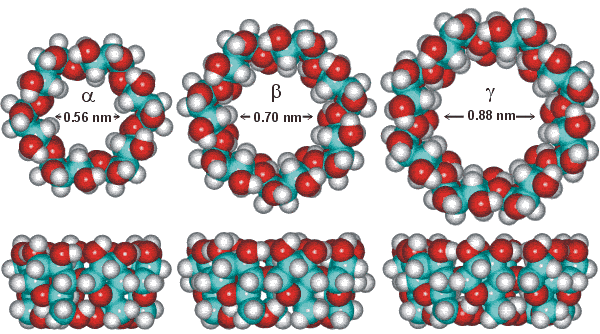
Natural Cyclodextrins
The most common cyclodextrins are alpha, beta, and gamma cyclodextrins having six (α), seven (β), or eight (γ) anhydroglucose units in the ring structure. Among them, beta Cyclodextrin is mostly common used.
Different sizes lead to different physicochemical characteristics for the respective molecules:
|
Characteristics |
Alpha (α) |
Beta (β) |
Gamma (γ) |
|
Number of glucose units |
6 |
7 |
8 |
|
Molecular weight |
972 |
1135 |
1297 |
|
Water solubility(g/100ml), 25° C |
14.5 |
1.85 |
23.2 |
|
Cavity diameter (nm) |
0.57 |
0.78 |
0.95 |
|
Height of torus (nm) |
0.78 |
0.78 |
0.78 |
Chemically modified Cyclodextrins
Cyclodextrins can be modified by various procedures such as:
Substituting one or more hydrogen atoms in the primary and/or secondary hydroxyl groups (esters, ethers, glycosylcyclodextrin)
Substituting one or more primary and/or secondary hydroxyl groups
Chemically modified Cyclodextrins (CDM's) exhibit substantially increased aqueous solubility with concomitant retention of the inclusion complexing properties of the starting Cyclodextrin. They therefore appear to offer specific applications within various industries, such as foods, pharmaceuticals, personal care/cosmetics, diagnostics, etc. Hydroxyalkyl b Cyclodextrins such as Hydroxypropyl b Cyclodextrin are examples of those chemically modified Cyclodextrins.
Natural Alpha Beta Gamma Cyclodextrin
Natural Beta Cyclodextrin,Natural Alpha Cyclodextrin,Natural Gamma Cyclodextrin
Shandong Binzhou Zhiyuan Biotechnology Co., LTD , http://www.zycydextrin.com